Online Gambling with Microgaming and AES-Encryption
Online betting companies tend to constantly improve the security systems, as web staking includes sending payment information (as credit card number, e-wallet accounts and etc.) to make a deposit. Such important data must be transferred safely without any unauthorized entries to it. That’s why, gambling giants as Microgaming use various protection methods to present the best service with a safe atmosphere.
The defense of the customer’s data includes using technologies like the Advanced Encryption Standard. AES for Microgaming casinos (also has a name of Rijndael), is a procedure of ciphering, used for transforming the info into a secure code for safe transmission throughout the web.
Definitions and Auxiliary Procedures
When getting acquainted with the AES, you will come across such definitions as:
- Block – a chain of bits;
- Cipher Key – cryptic digits, used for generating RK sets;
- Ciphertext – processed information after encrypting;
- Key Expansion – a procedure of generating RK out from the CK;
- Round Key – characters made from the CK after launching the KEP;
- State – a transitional cipher outcome, formed as a rectangular sequence of bytes;
- S-box – a non-linear commutation chart;
- Nb – columns correlated with the State;
- Nk – words (consisting of 32 bits), compounds for the CK;
- Nr – rounds;
- Rcon[] – a massive, which consists of the 32-bit word.
There are also auxiliary processes (functions) as:
- AddRoundKey () – a process in the ciphering (and inverse encrypting), when there is an RK, added to the State, with the help of the XOR program;
- InvMixColumns () – a process in the ciphering, which is the inverted operation of MixColumns ();
- InvShiftRows () – a function, inverted to ShiftRows ();
- InvSubBytes () – an alteration in the ciphering, inverted to SubBytes ();
- MixColumns () – uses State files and shuffles their content to create new columns;
- RotWord () – a function, which launches a cyclic reinstalling of the four-byte word (during the KEP);
- ShiftRows () – triggers dislocating (in cycles) of the last 3 rows of the State;
- SubBytes () – a part of the encryption technique, that uses a non-linear byte commutation chart (S-box) for each of the State bytes separately;
- SubWord () – one of the KEP functions, which uses a 4-byte word and applies an S-box for producing a ciphered word.
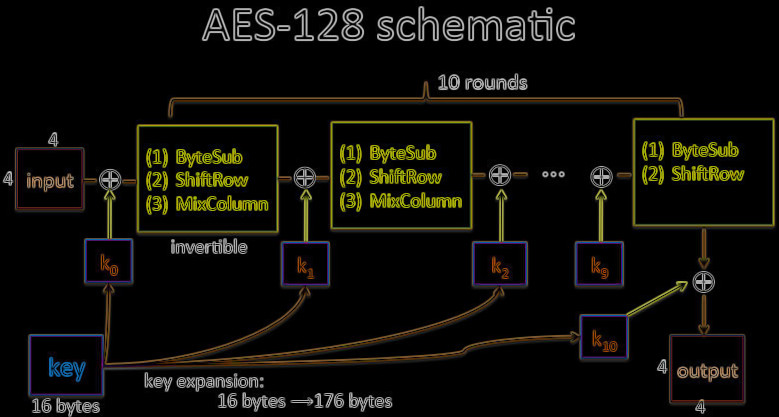
How AES Works in Microgaming Casinos
It has features and peculiarities of the iterative cipher. The work of such algorithm relies on substitution-permutation processes. It is formed by a set of conjunct procedures, several of which include substituting incoming data by particular outputs and other include shuffling bits.
Besides, every calculation uses bytes (when working with AES). Thus, 128 bits will be 16 bytes. This method allows encasing the data into 4 columns with 4 lines for enabling matrix computation. In such technique, the quantity of rounds can vary due to the size of the key.
Encryption
It has several layers of complexity to provide a good securing of the information. The encryption includes repeated periods which consist of 4 parts (sub-procedures). Such process (by steps) looks this way:
- Extracting the suite of RKs from the CK;
- Connecting the State sequence with the block data;
- Adding the initial RK to the first State array;
- Launching 9 cycles of the State manipulation;
- Performing the last (10th) one;
- Copying completed ciphertext.
SubBytes ()
Everything begins with an action of the AES structure, which is called SubBytes. On this stage, the 16 incoming bytes are replaced with the assistance of S-box (a special chart with fixed values), that is given as a pre-set. The outcome will be in a form of a matrix.
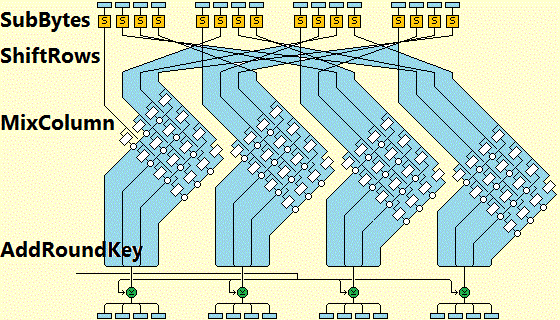
ShiftRows ()
When switching to this process, the 4 lines of the block will be shifted to the left. Any characters, that occurred to be out, appear then on the right side. Shifts perform in such way:
– 1st row – without alterations;
– 2nd – 1 character moves to the left;
– 3d – 2 characters;
– 4th – 3 characters.
In the end, there will be a new matrix block.
MixColumns ()
Every column, having 4 bytes, is then altered with a special function. It takes the original 4 bytes and displays completely new ones, which will commute the first digits. As a result, there will be another matrix with substituted bytes.
AddRoundKey ()
At this point, 16 bytes equals 128 bits and then with the help of XOR are attached to the RK. In case, it is the final round, you can consider the result as the ciphertext. Or if there are more steps to go, these 128 bits will be interpreted as 16 bytes and further cycles will start.
Microgaming Casinos Decryption Process
The decryption operation in playhouses powered by Microgaming is quite similar to the encryption, but just like an inverted version. Therefore, there will be the same stages and they will be launched in the opposite order.
Python Implementation of the Key Expansion Algorithm
When executing the code (see below) choose only these sizes: 128, 192 or 256. However, you may enter any number of digits you want, but if the length is shorter, the key will be completed to the required size by adding “0”. And, when you enter more numbers than needed, the script will use only the necessary quantity of characters.
